If you’ve already connected your GitHub integration via OAuth in GitKraken, you’re good to go!
GitHub is changing its security policy and will no longer allow username/password-only access. This change goes into effect on August 13th, 2021, and affects all desktop Git applications that offer a GitHub integration, including GitKraken.
Users who have already authenticated to GitHub using OAuth will be unaffected. OAuth is the default connection method within your GitKraken profile settings.
However, if you have been relying on a username and password to connect GitHub with GitKraken, now is the time to transition to OAuth, SSH, or using a PAT.
Connecting GitKraken to GitHub with OAuth
To connect to GitHub via OAuth, or to double-check that you’ve already done:
- Open GitKraken
- Open the Preferences menu (using the gear ⚙️ icon in the upper right), and click on Integrations from the left-hand menu
- Click on GitHub to reveal your connection status.If you have already connected previously, your status will show “Connected” and there is no further action needed. If you are not already connected it will look like this:
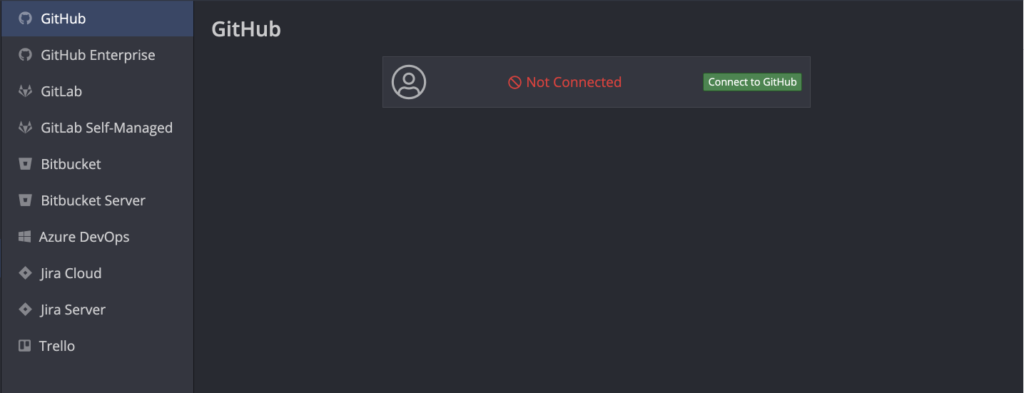
- Click “Connect to GitHub”
- In the new web browser window that opens, click on “Continue authorization”
- Follow the process on the GitHub login page to log into your GitHub account
If successful, the next screen should say: “GitHub and GitKraken are good to go!” 🎉
Reminder: GitKraken allows for multiple profiles, each with its own settings and preferences. Make sure you check the connection for each profile to avoid surprises when GitHub enforces this change.
For more information and further details about GitKraken’s GitHub integration, please see our Support documentation.
Now, if you just needed to establish or verify your GitHub connection, your work here is done. But if you want to dig a little bit further into this change, we invite you to read on…
GitHub Authentication Primer
GitHub is one of the most popular online collaboration platforms for software developers to track and share code. One of the reasons for its popularity is the number of local development tools, CI/CD pipelines, and all manner of applications that easily integrate with the platform. GitHub has made it very easy for users to connect with various integrations, allowing developers to choose the authentication path of their preference.
Prior to this upcoming GitHub authentication change, users had multiple connection paths to choose from:
- Username and password
- SSH keys
- Personal access tokens
- OAuth tokens
- GitHub App tokens
Personal access tokens and OAuth tokens look very similar and serve the same purpose. Both are tied to the user who requests the token, meaning they will have the same permissions as the user. The difference really comes down to concept, as well as the personal preference to manually manage account credentials.
Personal access tokens need to be generated from within a service, like GitHub, and they are managed and shared manually.
With OAuth, you authorize an app to talk to a service on your behalf. This is done through a handshake between the remote server and the local machine; the person authorizing may never see the actual credentials generated.
Both personal access tokens and OAuth authorization processes are very secure, with both typically granting permissions for the whole account at once, including any repositories the user or their organization owner can access.
GitHub App tokens, on the other hand, are used to grant specific privileges to an app or integration without providing wider access. As these are app-specific, they grant permissions to organizations, but limit which repos can be accessed by the authorized service. GitHub Apps also remain installed if the person who set them up leaves the organization or otherwise loses access.
Changes to the GitHub Authentication Process
As of August 2021, the first option on that list—username and password— will be eliminated to push the world toward a more secure internet.
Beginning August 13, 2021, we will no longer accept account passwords when authenticating Git operations on GitHub.com. Workflows affected: Command-line Git access Desktop applications using Git Any apps/services that access Git repositories on GitHub.com directly using your password
You can read more about this in detail on the GitHub blog.
Scheduled GitHub Brownouts on June 30 and July 28
Before August 13, GitHub will also be scheduling ‘brownouts’ of username/password authentications on June 30 and July 28 in order to test the change, as well as to “encourage affected customers to update their authentication method” prior to the official change.
As to why they are making this change, once again we can cite their blog post:
Tokens offer a number of security benefits over password-based authentication:
1. Unique – tokens are specific to GitHub and can be generated per use or per device.
2. Revocable – tokens can be individually revoked at any time without needing to update unaffected credentials.
3. Limited – tokens can be narrowly scoped to allow only the access necessary for the use case.
4. Random – tokens are not subject to the types of dictionary or brute force attempts that simpler passwords that you need to remember or enter regularly might be.
GitKraken is the Key to a Better and More Secure Workflow
If you read this article and have not already downloaded GitKraken, now is your chance. Integrating GitKraken with Github lets do all this and more:
- Create repositories on GitHub account including .gitignore and license
- Automatically generate an SSH key pair and add it to GitHub
- Fork repositories from GitKraken
- Save authentication into profiles
- Clone from GitHub repo list
- Create and Manage Pull Requests
Enjoy all the incredible features GitKraken has to offer and download now.

 GitKraken MCP
GitKraken MCP GitKraken Insights
GitKraken Insights Dev Team Automations
Dev Team Automations AI & Security Controls
AI & Security Controls